

Take a deep breath, and let’s dive in…
Patrick Burwell, www.Burwell.tech
This set of tools allows enterprise security administrators to download, analyze, test, edit and store Microsoft-recommended security configuration baselines for Windows and other Microsoft products, while comparing them against other security configurations. -Microsoft Security Compliance Toolkit 1.0
https://www.microsoft.com/en-us/download/details.aspx?id=55319
If you need to ‘Analyze, refine, and create Group Policies’ the first thing you need to do is download the policy analyzer in the security toolkit linked above. Then follow these procedures we provided that we have tweaked and checked against our experience. (Our thanks to Elon Musk’s Grok 3 and DuckDuckGo.com’s Duck.ai for helping us keep this article clean and logical. – Burwell.tech)
Prerequisites: You need administrative privileges and Remote Server Administration Tools (RSAT) installed. This guide applies to Windows Server 2016 or later in an Active Directory domain.
Step-by-Step Procedure to Use Policy Analyzer
1. Download and Install the Security Compliance Toolkit
- Visit the Microsoft Download Center:
https://www.microsoft.com/en-us/download/details.aspx?id=55319
(Grok’s download link was to a quite old TechNet blog, so we updated the link to be direct) - Download the Microsoft Security Compliance Toolkit 1.0 package, which includes the Policy Analyzer tool and the latest security baselines.
- Extract the downloaded
.zipfile to a folder on your system (e.g.,D:\SCT).
Recommended Practice: Whenever you download a tool, NEVER extract or expand from the original file. Make a copy and then extract from the copy source; That is a good practice to get into. We recommend, as another good practice, to keep the extracted/expanded zips in d:\utils and then install from the d:\utils volume and folder to your desired location. And we never recommend installing anything not native to the server on the C, or OS, volume.
We always recommend running your tools from a robust system that has a direct fiber or a Gigabyte (GB not Gb)* ethernet connection from the data center where your Infrastructure Master is running.
2. Locate the Policy Analyzer Tool
- In the extracted or expanded folder, find the
PolicyAnalyzerdirectory. The main executable isPolicyAnalyzer.exe. - Ensure you have administrative privileges on the system, as the tool requires access to all policy settings.
3. Prepare Group Policy Objects (GPOs) or Baselines
- Gather GPOs: Export the GPOs you want to compare. You can do this using the Group Policy Management Console (GPMC):
- Open GPMC (
gpmc.msc). - Navigate to the GPO you want to analyze.
- Right-click the GPO and select Back Up.
- Then copy the GPO backup to a folder you will work from.
(e.g.,D:\GPOBackups). - Include Baselines: The toolkit includes Microsoft-recommended security baselines (e.g., for Windows 10 (1507) to Windows 2025), and you can also download more recent baselines from the same download source. These OS specific baselines are located in the extracted toolkit folder under directories like
Baselines, and online at the download location as well, under the ‘Details’ section. - Ensure all GPOs or baselines you want to compare are in a compatible format (e.g.,
.inffiles or GPO backup folders).
- Open GPMC (
Recommended Practice: We do recommend for experienced engineers to always use backpack drives, not usb sticks, for the D drive mapping. Then back that drive up to whatever SAN storage your client uses.
4. Launch Policy Analyzer
- Run
PolicyAnalyzer.exeas an administrator:- Navigate to the
PolicyAnalyzerfolder on the D Volume. - Right-click
PolicyAnalyzer.exeand select Run as administrator. You are going to want to be logged in with the ‘God-mode’ account, or ‘RunAs’ the executable.
- Navigate to the
Recommended Practice: You do not need a domain controller to run Policy Analyzer or analyze Group Policies from a laptop. A laptop running Windows 11 with Remote Server Administration Tools (RSAT) installed is sufficient, provided you have sufficient administrative credentials for the Active Directory (AD) domain and network access to a domain controller. Policy Analyzer, Group Policy Management Console (GPMC), GPResult, and PowerShell can all be run from a client machine (like a laptop) without requiring you to log into or directly manage a domain controller.
5. Add Policies to Compare
- In the Policy Analyzer interface:
- Click Add to import policies.
- Select Add files from GPO or Add files from folder to include:
- GPO backups (from Step 3).
- Microsoft baseline
.inffiles from the toolkit.
- Browse to the folder containing the GPO backups or baseline files and select them.
- Repeat for all policies or baselines you want to compare.
- Assign a friendly name to each policy for easier identification (optional, but highly recommended by Burwell.tech).
Recommended Practice: When managing Group Policy you can ‘get in the weeds’ fast, so be patient and take your time to be very methodical, because you will have to explain the mess you find and have the confidence that you know what you need to do to ‘fix’** what you identify. So document your steps and be careful to be confident.
6. Select Policies for Comparison
- In the Policy Analyzer window, check the boxes next to the policies or baselines you want to compare.
- Ensure at least two policies are selected to enable comparison.
7. Analyze the Policies
- Click the Compare button to analyze the selected policies.
- The tool will generate a comparison report, highlighting:
- Settings that are identical across policies.
- Settings that differ, including specific values for each policy.
- Settings unique to one policy or another.
NOTE: This Policy Analyzer tool is run OFFLINE and does not edit the policies themselves, so there is no impact
8. Review the Comparison Results
- The results are displayed in a table format within the Policy Analyzer interface.
- Columns show:
- Policy settings (e.g., registry keys, security options).
- Values for each selected policy.
- Differences highlighted for easy identification.
- Use the Filter or Search options to focus on specific settings (e.g., password policies, account lockout settings).
9. Export or Save Results (Optional)
- To save the comparison for documentation or further analysis:
- Click File > Export (or similar option, depending on the version).
- Choose to export as an Excel spreadsheet, CSV, or HTML file.
- Save the file to your desired location.
10. Analyze and Act on Findings
- Review differences to identify deviations from Microsoft’s recommended baselines or conflicts between GPOs.
- Adjust GPOs as needed using GPMC or other tools to align with security best practices or organizational requirements.
- Re-run Policy Analyzer to verify changes.
11. Additional Steps (Optional)
- Policy Viewer: Use the View button to inspect individual policy settings in detail.
- Compare with Local Policy: Analyze GPOs against the local machine’s security settings by selecting the local system as a policy source:
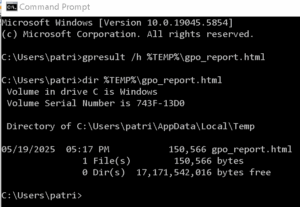
Use GPResult: To check which GPOs are applied to your computer and user, open Command Prompt as an administrator and run `gpresult /r`. For a detailed HTML report, use `gpresult /h %TEMP% gpo_report.html` from the CMD interpreter, and the open the file in a browser. - Custom Baselines: Create custom
.inffiles for comparison by exporting local security policies usingsecpol.msc(Security Policy snap-in). - Check
ConcurrentCallLimitis not being exceeded:
# Load the Group Policy module
Import-Module GroupPolicy
# Get the current ConcurrentCallLimit setting
Get-GPRegistryValue -Name "Default Domain Policy" -Key "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" -Value "ConcurrentCallLimit"- On the Non-GC Infrastructure Master Domain Controller***, the log to watch for
ConcurrentCallLimiteventID 1129:
‘Applications and Services Logs -> Microsoft -> Windows -> Group Policy -> Operational’. Note that In this log, you can look for events that indicate problems with Group Policy processing, such as timeouts or failures to apply policies, which may be related to exceeding theConcurrentCallLimit. Specifically, Event ID 1129 can indicate that the Group Policy processing is being throttled due to too many concurrent requests.
Other Notes and Tips
In no way can this be considered comprehensive, so do your research…
- System Requirements: Policy Analyzer runs on Windows operating systems (e.g., Windows 11, Windows Server 2016). Ensure .NET Framework 4.5 or later is installed.
- Documentation: The toolkit includes a
Documentationfolder with guides (e.g.,PolicyAnalyzer.docx). Refer to these for advanced usage or troubleshooting. - Best Practices:
Don’t expect you will be able to do these… just sayin’ -Patrick- Test GPO changes in a non-production environment first. <– CRITICAL
- Regularly compare policies against Microsoft’s latest baselines to maintain compliance. <– CRITICAL
Policy Analyzer compares security settings but does not modify GPOs directly, and, when run as directed, analyzes offline, with no impact to the network and Active Directory | You will need to use the Group Policy Management Console , GPMC.msc, or other tools, for editing Group Policies.
We don’t call the fact that the policy analyzer cannot edit Group Policy a limitation, but we call that a “Thank God it doesn’t change anything” tool!!!
Tools for Group Policy Editing
- Group Policy Object Editor (gpedit.msc): This is a local tool that allows you to edit Group Policy settings on a local computer. It is primarily used for configuring local policies and is not suitable for editing domain-level Group Policies.
- Windows PowerShell: PowerShell provides cmdlets for managing Group Policies, such as
Get-GPO,New-GPO,Set-GPLink, andRemove-GPO. You can use these cmdlets to create, modify, and link Group Policies programmatically. - Group Policy Preferences: This feature, which is part of the Group Policy Management Console, allows for more granular control over settings and configurations, such as drive mappings, printer connections, and scheduled tasks. It provides a user-friendly interface for managing these preferences.
- Advanced Group Policy Management (AGPM): This is an add-on for the Group Policy Management Console that provides enhanced management capabilities, including version control, change control, and role-based delegation for Group Policies.
- Local Security Policy (secpol.msc): This tool allows you to manage security settings on a local computer, including user rights assignments and security options. It is useful for configuring local security policies.
- Group Policy Modeling: This feature within GPMC allows you to simulate the effect of Group Policy settings on users and computers without applying the policies. It helps in understanding how policies will affect the environment.
- Group Policy Results (gpresult): This command-line tool provides information about the Group Policies applied to a specific user or computer. While it does not allow for editing, it is useful for troubleshooting and verifying policy application.
- Third-Party Tools: There are various third-party tools available that can assist with Group Policy management, such as Specops Gpupdate, GPOAdmin, and others. These tools may offer additional features or simplified interfaces for managing Group Policies.
If you encounter issues, or need specific settings analyzed, let me know and I can provide further guidance, or, for additional self-research, refer to the Microsoft Security Compliance Toolkit documentation at the download link at the top of this article. -Burwell.tech
More Microsoft Resources:
Learn more: aka.ms/baselines | Download the Security Compliance Toolkit: aka.ms/SCT |
*GB or Gb: The correct measurement for internet speed is typically in gigabits per second (Gbps), while gigabytes per second (GBps) is used for data transfer rates in contexts like file transfers in data center environments and networks:
- Gbps (Gigabits per second): Commonly used to measure internet speeds and bandwidth.
- GBps (Gigabytes per second): Used to describe data transfer rates, such as when transferring files between devices.
To clarify, 1 GBps is equal to 8 Gbps, since there are 8 bits in a byte.
** ANYONE with any decent amount of experience dealing with a fouled Group Policy knows that to ‘fix’ the Group Policy will mean you will have to break it. Nothing ever gets fixed that you don’t have to break first. I recommend making a copy first before every applying changes, then apply the changes to the copy you CLEARLY LABEL and date, something like this:
Original: Default Domain Controllers Policy
Changed: 20250519 Default Domain Controllers Policy
Then you enable the changed one and disable the original.
*** Should my Infrastructure Role Domain Controller NOT be a Global catalog server?
Yes, for Group Policy reasons, it is generally advisable to have the Infrastructure Master (IM) role holder not be a Global Catalog (GC) server, especially in a multi-domain environment. Here are the reasons why:
- Role Functionality: The Infrastructure Master is responsible for updating references to objects in other domains. If the Infrastructure Master is also a Global Catalog server, it holds a complete replica of all objects in the forest. In this case, it does not need to perform updates for cross-domain references, which can lead to potential issues with object updates and group memberships.
- Throttling and Performance: A Global Catalog server is often under more load because it handles queries for all objects in the forest. If the Infrastructure Master is also a GC, it may become overloaded, which can affect its ability to process Group Policy efficiently. This can lead to delays or failures in applying Group Policies, especially if there are many concurrent requests.
- Event Monitoring: If you are monitoring Group Policy events, having the Infrastructure Master as a non-GC can provide clearer insights into issues related to Group Policy processing. This is because the IM will be more focused on its role without the additional load of GC queries.
- Best Practices: Microsoft recommends that in a multi-domain environment, the Infrastructure Master should not be a Global Catalog server unless all domain controllers in the domain are also Global Catalog servers. This is to ensure that the IM can perform its role effectively without the complications introduced by being a GC.
In summary, for optimal Group Policy processing and to avoid potential issues, it is generally better to have the Infrastructure Master not be a Global Catalog server, particularly in environments with multiple domains. This separation allows each role to function more effectively and reduces the risk of performance bottlenecks.
Final note for the Rookies:
Know that MANY MANY domains have issues with replication. In 30 years we have not ever seen one network, specifically with a server count greater than 300 servers, not one environment that did not have replication issues. So, when you apply the enabled policy DO NOT ENFORCE THE CHANGES. Let them replicate as normal. Why? A number of reasons but mainly, when you force the replication you are forcing a replication that may have never succeeded. I know the answer will be, “Well, fix the replication issues first.” And to that we say from experience, “Yeah, good luck making the Group Policy fixes wait until you have fixed your AD replication issues.”
“Listen. They key to such a seemingly daunting task is to breathe, to relax, and take one step at a time. If you feel rushed you will mess it up so step back when you get anxious. Don’t let anyone rush you or you should consider telling them to do it themselves. And, for God’s sake, learn how to back it all up, and how to restore the Group policies, first, before you make a single change.” -Patrick Burwell
We used Duck.ai to help us with the details on this article

Leave a Reply